Understanding the FedRAMP Continuous Monitoring Process
This article will provide a detailed exploration of the vulnerability scanning and reporting process during Continuous Monitoring (ConMon), shedding light on the specific challenges encountered by cloud service providers (CSPs) in this area. FedRAMP mandates CSPs to conduct monthly vulnerability scans and maintain a Plan of Action and Milestones (POAM) to promptly monitor and address vulnerabilities. Monthly reporting responsibilities related to vulnerability scanning include submitting scans, updating the POAM, maintaining current system inventories, and documenting any deviation requests. These obligations are not only crucial for maintaining compliance but also extend to the CSP’s authorizing agency, whether it be the Joint Authorization Board (JAB) or the FedRAMP Program Management Office (PMO).
ConMon, as outlined in the FedRAMP Continuous Monitoring Strategy Guide, requires CSPs to diligently monitor their security controls, conduct periodic assessments, and ensure the continuous adequacy of their service’s security posture. Critical activities within ConMon, such as Annual Assessments, Penetration Testing, Vulnerability Scanning, and Access Reviews, play pivotal roles in providing the Authorizing Official (AO) with essential risk-related information for making informed decisions. Despite the apparent simplicity of these tasks, they consistently present challenges for organizations of varying sizes, ranging from fortune 100 CSPs to small startups.
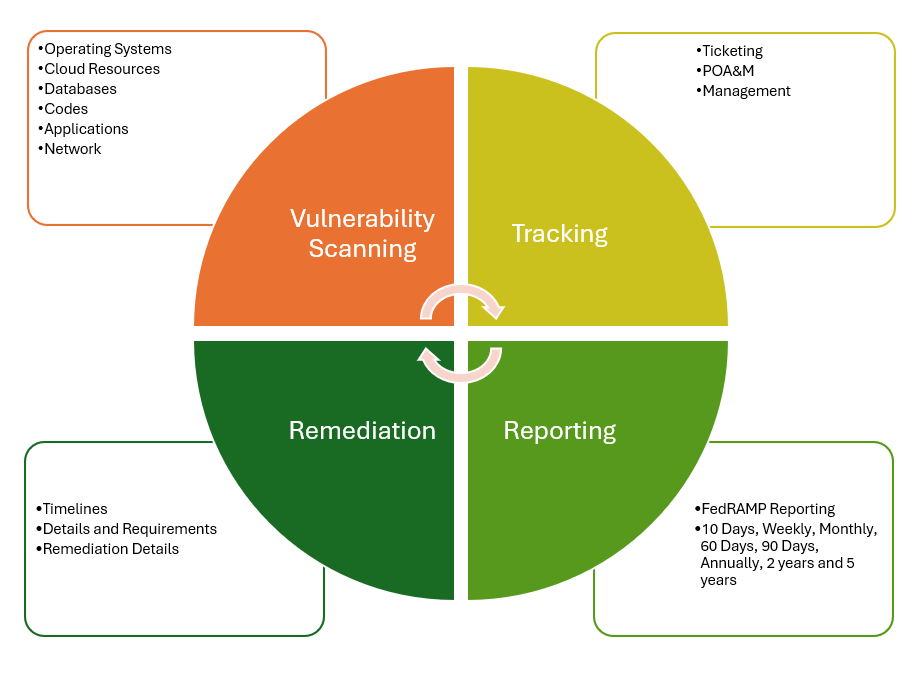
Vulnerability Scans and Requirements
Maintaining comprehensive vulnerability scanning practices within the framework of FedRAMP Continuous Monitoring (ConMon) is imperative for effective IT asset management. It is essential to properly scan and accurately list all organizational IT assets in a system component inventory to effectively manage them. Moreover, maintaining an up-to-date system component inventory is crucial to stay abreast of any changes or additions to the assets.
A critical aspect of ConMon involves conducting thorough monthly scans of the information system to identify and address any vulnerabilities that may exist within the system. This includes conducting scans across various components such as databases, web applications, operating systems, networks, cloud resources and application containers. While there are some guidelines available on container scanning, partnering with FabricLake can offer expert guidance and support in executing appropriate scans tailored to the specific requirements of the system.
Engaging with a specialized ConMon team ensures comprehensive scanning and monitoring of system assets, thereby enhancing the overall security posture of the organization. By leveraging expert guidance and support, organizations can effectively identify and mitigate vulnerabilities, ultimately strengthening their defense against potential cyber threats and ensuring compliance with FedRAMP requirements.
Tracking of Vulnerabilities and Tasks
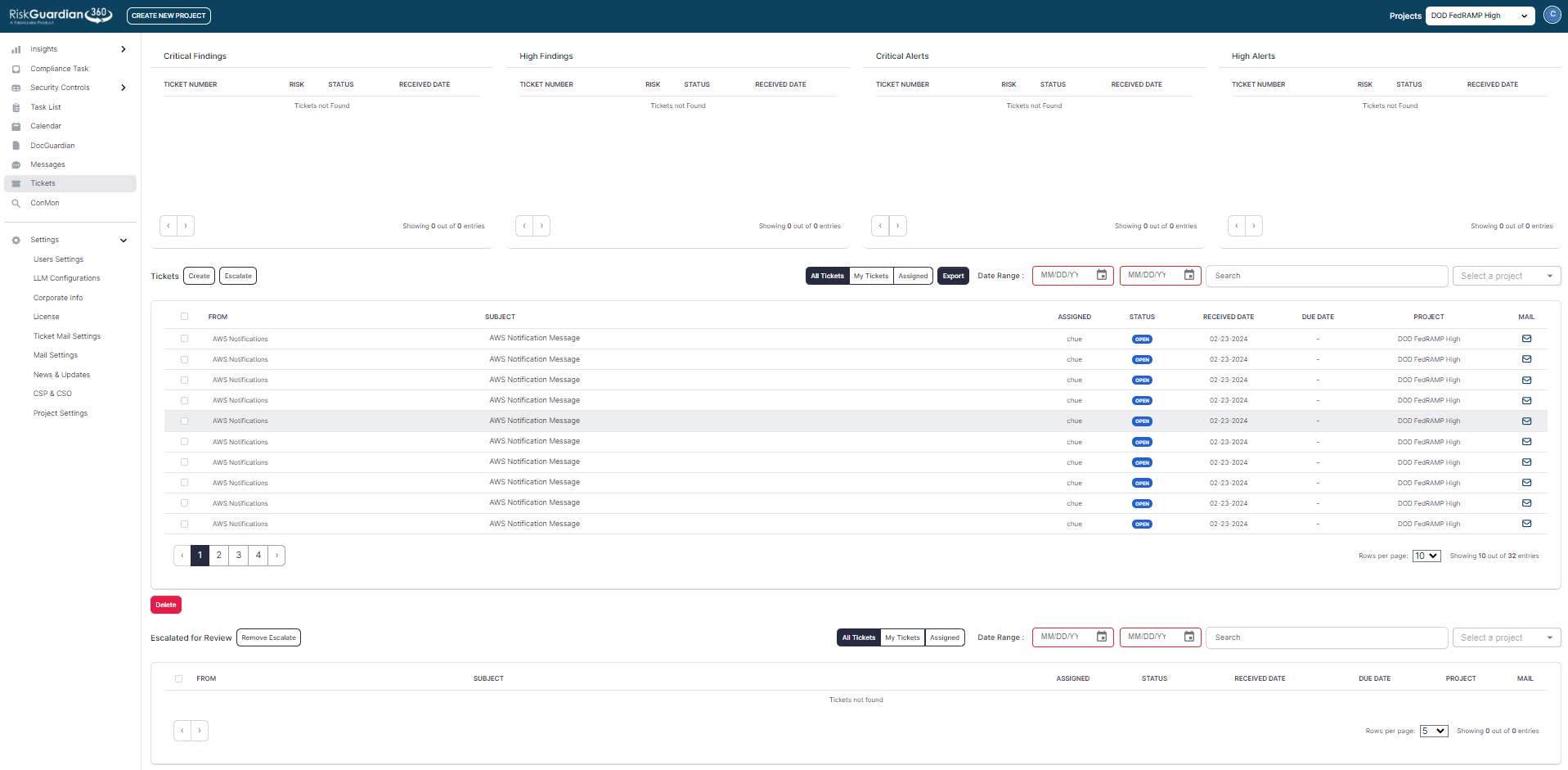
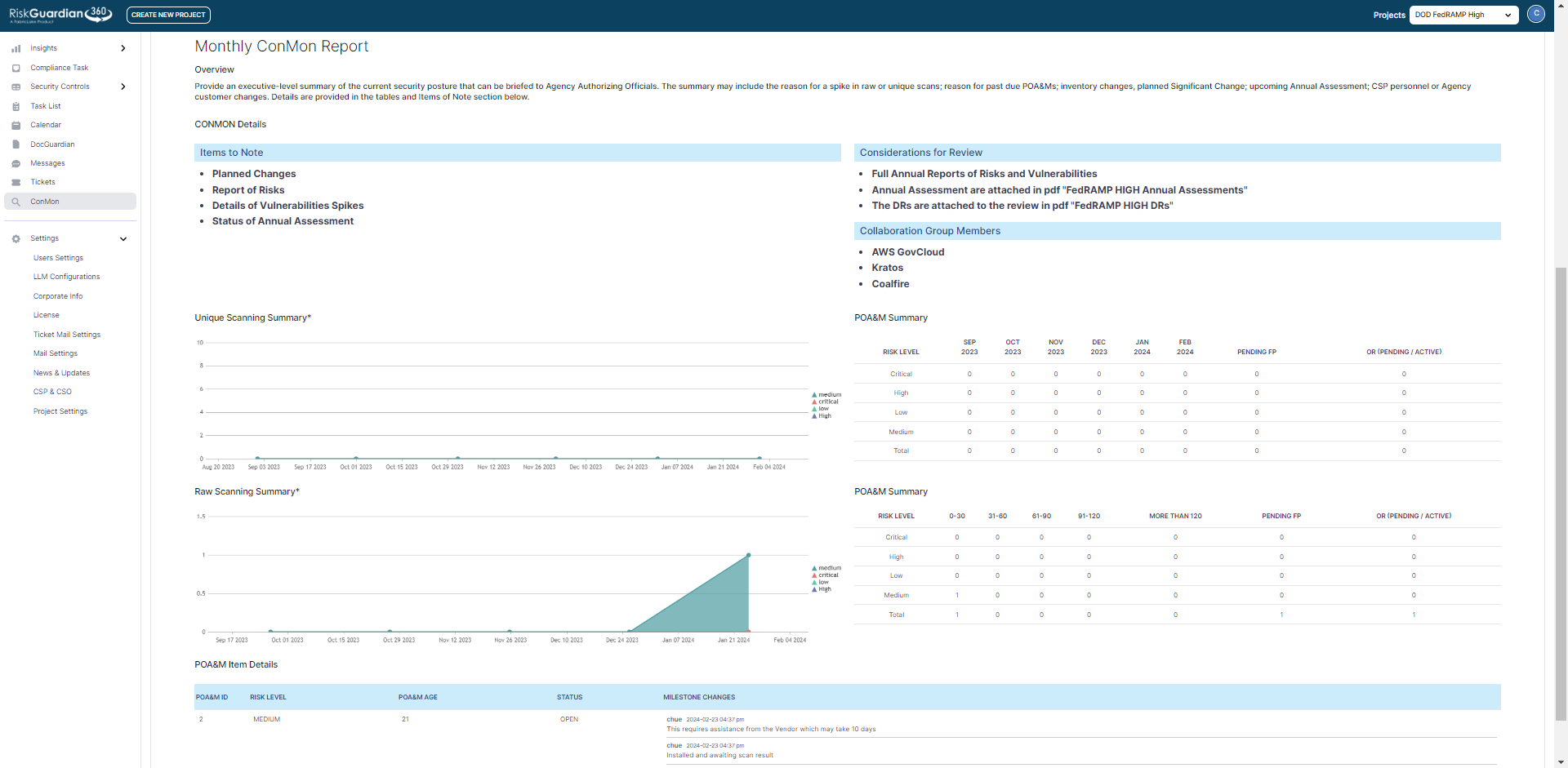
We leverage RiskGuardian360 to effectively monitor vulnerabilities and oversee their remediation process within the Authorization Boundary. This specific task presents challenges for numerous CSPs, particularly those relying on unauthorized ticketing systems for task and vulnerability management.
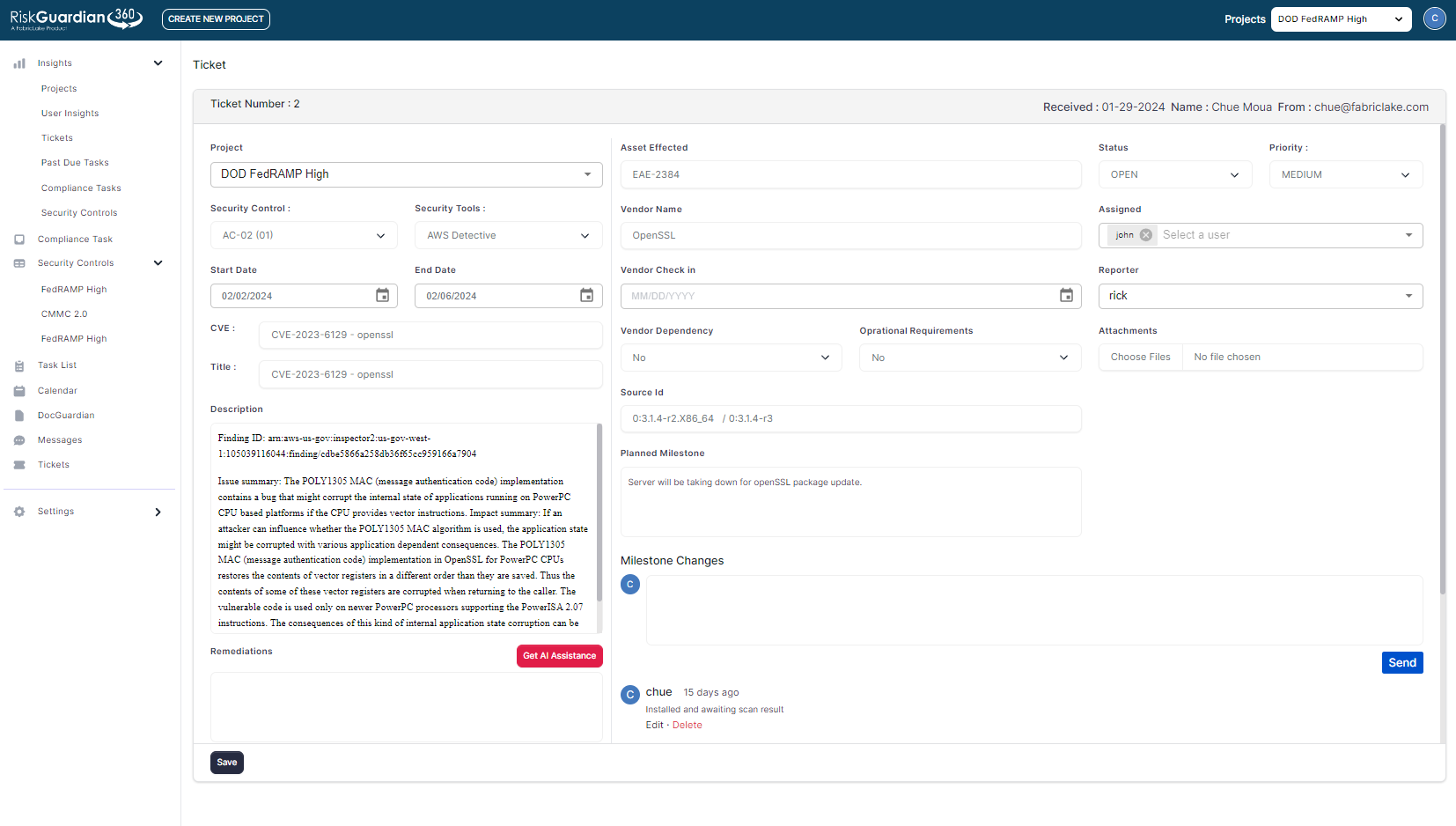
The Plan of Action and Milestones (POAM) serves as a vital document for tracking all identified vulnerabilities within the system, offering the Authorizing Official (AO) insight into changes that could potentially impact the system’s overall risk posture. Vulnerability scanning results are logged within a ticketing system, which then integrates into the POAM and encompasses various defined fields. Critical severity vulnerabilities necessitate immediate remediation, while others are allotted specific timeframes, such as high severity within 30 days, moderate severity within 90 days, and low severity within 180 days. Monitoring these vulnerabilities and ensuring none become overdue can prove to be a challenging endeavor.
This leads us to deviation requests, which serve as a mechanism for submitting justifications and evidence countering the original risk assessment or due date. There are three types of deviation requests: False Positive, Risk Adjustment, and Operational Requirement.
- A False Positive request indicates that there is no actual risk posed to the system.
- Risk Adjustment implies that the risk is less severe than initially identified by the scanning tool.
- Operational Requirement requests signify that the risk will persist, often with mitigating factors, based on business or system requirements outweighing the identified risk.
Many CSPs utilize a ticketing system like RG360 to communicate identified vulnerabilities with various teams, including DevOps, SREs, SOC, NOC, and developers, seeking their expert assistance. Properly employing these deviation request types with well-articulated justifications and satisfactory supporting evidence can significantly mitigate the perceived risk associated with the system, thereby averting disciplinary actions from the FedRAMP PMO due to overdue vulnerabilities or an increase in the unique vulnerability count.
Remediation Requirements
Within RiskGuardian360, as soon as a vulnerability is identified, it is promptly assigned to a user or technical team responsible for its remediation. Establishing robust internal vulnerability management policies and procedures is crucial for CSPs to effectively meet FedRAMP’s remediation requirements. These policies should clearly identify stakeholders, set remediation thresholds, and prioritize vulnerability management within the organization.
Conducting scanning early in the scan cycle is essential for CSPs to identify issues promptly and prevent any mishandling of continuous monitoring tasks. Early scanning also enables compliance personnel to proactively develop deviation requests that may address issues nearing their overdue status. By addressing vulnerabilities in a timely manner and having well-defined policies in place, CSPs can enhance their ability to meet FedRAMP’s remediation requirements and maintain compliance effectively.
Understanding the Reporting Structure
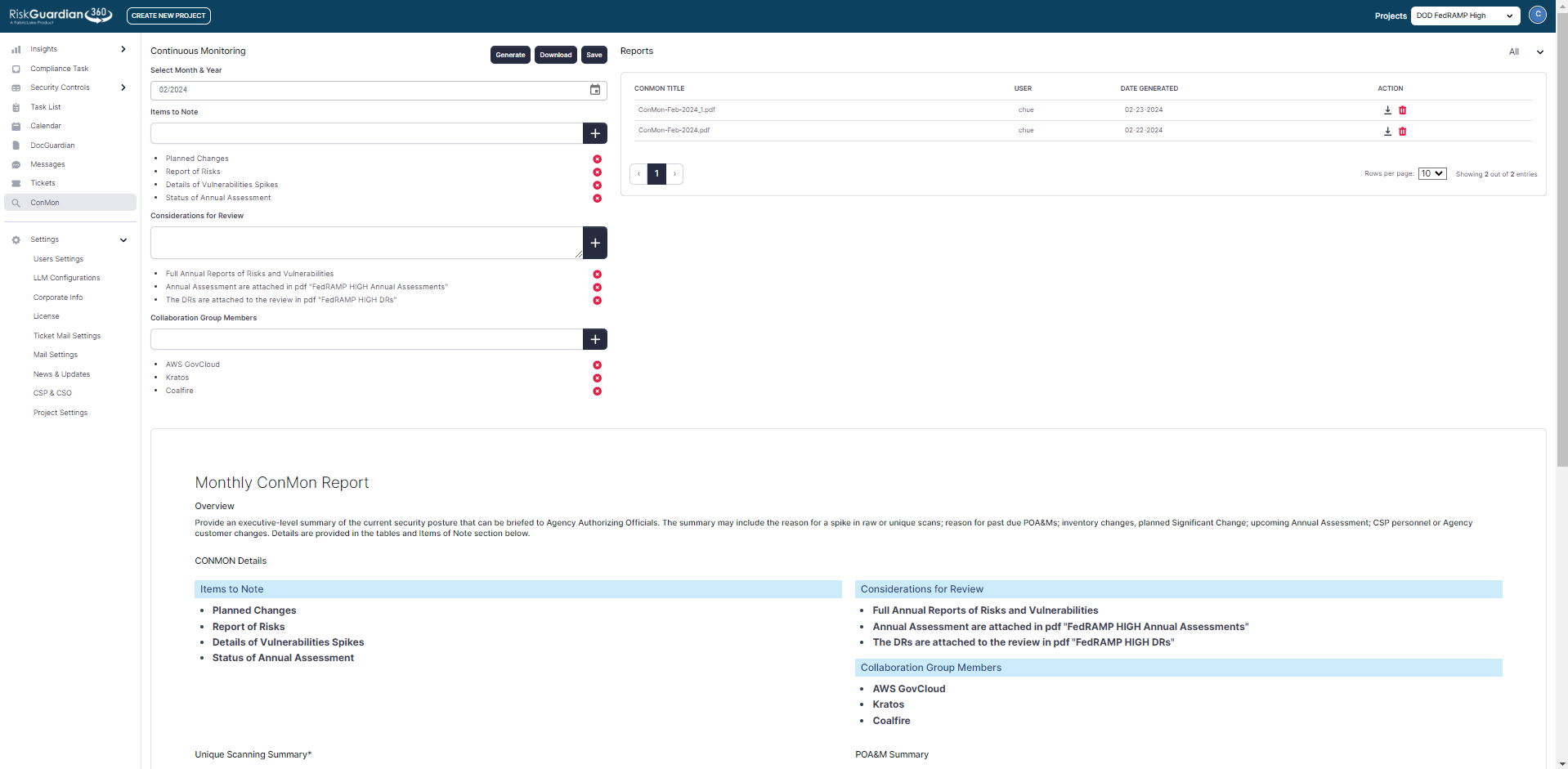
RiskGuardian360 plays a crucial role in assisting CSPs in reporting their system’s security status to their authorizing agency, whether it’s the Joint Authorization Board (JAB) or the FedRAMP Program Management Office (PMO), on a monthly basis. In fact, RG360 actively aids in compiling all necessary documentation required for the reporting process.
Regarding vulnerability scanning, CSPs are required to submit various components including scans, evidence of mitigating high-risk vulnerabilities, the Plan of Action and Milestones (POAM), up-to-date system inventory, and documented deviation requests. It is imperative for CSPs to collaborate closely with their authorizing organization to determine the specific method and requirements for submitting scans and evidence. This collaboration ensures alignment with the agency’s preferences and facilitates a smooth and compliant reporting process.
Want to see a demo or do a free 30 day proof of concept?
Takes 5 minutes to be up and running with ready made templates available to help you jumpstart the federal compliance journey!
Share This Article
How can I help?
With over 2+ decades of experience in the field of IT and compliance, I have successfully overseen multiple FedRAMP certifications and a dozen ATOs within the realms of the DOJ and DOD.
“Chue is a brilliant technologist who is a SME for everything with InfoSec and Federal Government Compliance. He is incredibly diligent, hard-working and is able to easily discuss complicated technical matters with both experts and beginners. His can-do, humble attitude made it a distinct pleasure to work with and learn from him.”
Other endorsements…
“Working with Chue has been an honor. He’s incredibly knowledgeable and always travels out of his way to offer assistance and guidance. He made sure our systems were completely secure and gave us the peace of mind to focus on our responsibilities without worry of interruption.
Outside of a work capacity, Chue has been a positive and motivating force and he has a keen ability to instill trust.”
Experts who understands the Federal landscape
Imagine a world where organizations enthusiastically embrace cutting-edge AI technology, harnessing its power to gain profound insights into high-risk scenarios and propelling themselves toward their core business objectives with confidence!
Here at FabricLake, we take the charge in revolutionizing federal compliance solutions! We’ve masterfully entwined the power of artificial intelligence into the very essence of our compliance processes. This astute integration doesn’t just optimize workflows; it paves the way for seamless task management and issue resolution, all while upholding the highest industry standards. In the heart of our Federal Compliance division, AI has seamlessly woven itself into the fabric of our operations, giving birth to RiskGuardian360 – a specialized application that unleashes the full potential of AI to steer us towards our compliance objectives with unwavering determination. Join us in embracing this cutting-edge technology and watch your compliance needs transform into opportunities for excellence!








